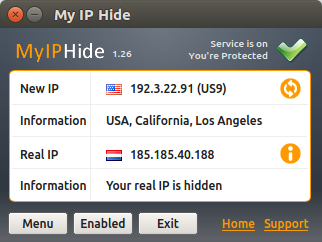
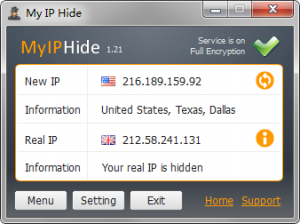
Server Proxies serve as intermediaries in between the web and the web user. They are quickly set upon the user’s network or computer, such as a business office. Server proxies were originally developed to speed web searching for caching proxies. They can also be used for spying, web privacy, and content filtering. You can always check your ip address at my ip .
Server proxies store often accessed resources that accelerate the load time and saving bandwidth.
Server proxy content filtering, used in nations, services, and schools, limit access to particular websites and pages by utilizing blacklisted website database or flagging websites which contain particular keywords.
Prominent Functions
Server proxies who prevent override the content filtering proxy guidelines for accessing to obstructed websites. Frequently, web tracking is tracked by search histories and IP addresses of checking visitors. A couple of proxy servers allow users to conceal their IP address behind proxies to anonymously search the web.
As confidential web proxies allow searching privacy, hostile proxies are all ears on web surfing of the user. Before striking the site, most reverse proxy servers send out online demands through a proxy.
As the traffic goes through, proxies secure the details, consisting of a password, before passing them into the site.
Benefits
Server proxies are firewall software mechanized which replaces a safeguarded host network’s IP address with momentary addresses for data traffic. It makes choices for confirming the customer or user’s IP address to develop a connection to remote computers.

Server proxies serve as intermediary or user interface to link 2 or more computers having different procedures, put at remote areas over the net. When users attempt to link to other users for connections, websites, and files available on the database, the proxy server examines the connection based on the remote computer’s existing settings.
Confidential proxies are a form of proxy servers, which resolve web form, known typically as CGI proxy. Instead of setting up the server address in the browser, users just have to browse to the web page of the CGI/ Web proxy, where the proxy performance is then allowed for each searching session.
Confidential proxies are created to safeguard the privacy and privacy of web browsers from website operators, hostile federal governments, and web snoops. The software for confidential proxies is positioned on the proxy server.
Proxy Checker – The Very Best Way to Inspect Proxies.
Have you ever found yourself dealt with not with having trouble finding proxies, however within fact finding a way to inspect your proxies to validate that they work? There are 2 ways you can validate proxies in an effort to find the very best working ones.
The first way you can examine and confirm proxies is by means of many online proxy sites. Many proxy sites provide a free service in which you just copy and paste the proxies you wish to inspect and with the basic click of a button they are validated.
In confidential proxies, the web browser is linked to the server, which then links to the online server. The web server is unaware of your identity. It is just knowledgeable about the identity of the server. As the proxy server can’t determine your existence – you need to pick a reliable proxy server.
The moment the proxy server confirms that the conditions are satisfied, it makes the demand on the user’s behalf, developing the connection.