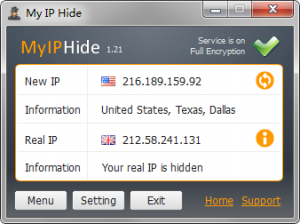
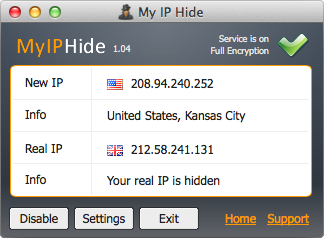
For added protection, F-Secure anti-virus software service blocks advertisers’ tracking services and warns of known websites as malware spinners. Search queries that search engines like Google store and assign to users also want to anonymize F-Secure. The tool opens a special search page from F-Secure. This is based on the Google search and incidentally, even without VPN subscription usable. Good: The Finnish software company promises not to store the IP addresses of users and works without user registration, and there is no limit on the volume of data. When using a US server, we measure a first-rate download speed and also good upload values. The F-Secure service is available in versions for OS X, Windows and Android. A one-year subscription for three devices costs 50 dollars. From myip this is very much possible.
Anonymous in the network with the proxy server
As virtual private networks, proxy servers also work. The user logs in on this server and borrows a virtual server address for the online surf session. Even proxy servers are often used to circumvent regional content restrictions, but like VPNs, especially in countries with deep web regulation, they are helpful in overriding censorship.
Although the use of a proxy server for obscuring the IP address is a common means, nevertheless there is always a higher risk than with a reputable VPN provider. If data is tapped via a proxy server, these are contrary to the use of VPN not encrypted.
Hide IP address with the Tor Browser
Hardly any name is more synonymous with anonymity on the Internet than the Tor browser. For years, it has been the app of choice for those who are more concerned about being spied online by governments, criminal hackers or businesses.
The Browser is a free open source tool that redirects your connection across multiple nodes around the world, not just obfuscating your IP address. What brings us to the great disadvantage of use: the speed? Or better: the lack of speed that comes from the different security layers.
Gate
“Tor” was originally an acronym and stood for The Onion Router project. The Tor network uses multiple encryption layers to hide data as well as its origin and destination. This helps to anonymize the data connection. Tor is the only way to access much of deep web.
Block Chain
Bitcoin is based on the concept of the distributed database, the so-called blockchain. It is a common transaction database of all Tor nodes in a system based on the Bitcoin protocol. To independently verify the copyright of any bitcoin amount, each node has its own copy of the blockchain.
Surf the web anonymously on the Internet with the Tor Browser Package
Each time you launch it, the program gets another IP address from the Tor network that differs from your actual one. The program is based on the company-proven Firefox ESR has integrated the Tor obfuscation as a central component as an add-on. Neither the browser nor the Tor add-on requires installation, and it is easily possible to run the secure-surfing browser in parallel to regular Firefox; despite the same process name firefox.exe. With the ever-active IP Disguise, websites are having a harder time recognizing you clearly and getting an idea of your online habits.